
IT- Network Security for Law Firms
How can I protect my information from any kind of risk, if I hire a virtual assistant in another country?
Nowadays, data protection has become an issue of concern for many companies due to the large number of hackers who have stolen information in recent years. In addition, the concern of giving access to abroad VA’s (virtual assistants), generates many doubts about how it should be handled properly.
Before hiring a VA it’s highly recommended that you, as the owner of your Law Firm, allocate budget and put in place all the «standard» security measures to avoid any cyber risk regardless of whether or not you consider hiring a foreign Virtual Assistant, since the information- that is confidential for you- lives inside your PC is on demand by any individual from the minute you use the Internet as a means of work.
This is what you will learn
ToggleWhat are the «standard» security measures recommended to avoid any cyber risk?
It is unavoidable to go a little bit into the IT-Network Security area since they are the experts that today have developed specific technology for data security, one of the most recognized companies in this area worldwide is CISCO, who has the most advanced protocols for data protection. Therefore, if you are looking for a very high level of data protection, you need to configure the following components in your office:
- Switch
- Router
- FireWall
- Internet Service
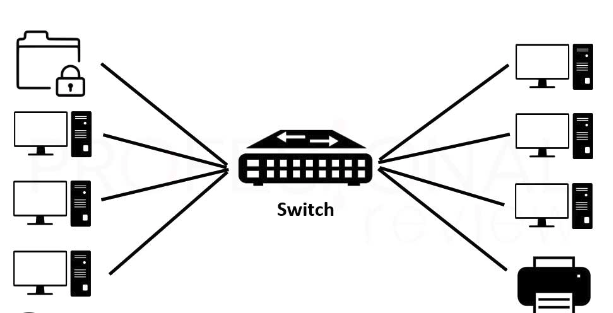
A network switch is an interconnection device used to connect all equipment on a network, including computers, consoles, printers and servers. Together with the cabling they form what is known as a local area network (LAN).
Thanks to a switch, all connected equipment can:
- File sharing
- Printer sharing
- Share the Internet connection.
The router is a device that allows interconnecting networks with different IP address prefixes. Its function is to establish the best route for each data packet to take to reach the network and the destination device. It is widely used to connect to the Internet since it connects the network of our home, office or any network to the network of our Internet provider. Most of the routers used for home and offices have other additional functions incorporated to the router, such as: wireless access point, which allows to create and connect to a Wifi network; modem, which converts analog signals to digital and vice versa; Switch, which connects several devices through cable, creating a local network. Also, some of them includes a Firewall which is a system designed to protect private networks from unauthorized and unverified access to an Internet connection.

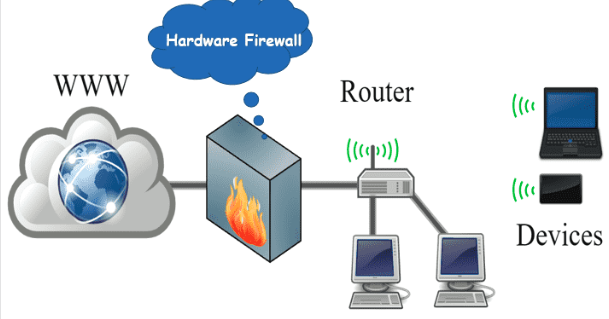
Firewalls protect your computer, or a number of computers on a network, from malware-filled websites or vulnerable open network ports. They help stop would-be attackers before they can do any damage. Network firewalls can be found in businesses, homes, schools and intranets, which are private networks within an organization. In addition, they can be configured to prevent network users from accessing external websites. For example, office managers can set up controls over their employees’ browsing habits by blocking certain websites to avoid distractions.
This component is the most important of all as it is the first «wall» a hacker faces when trying to penetrate your network.

The Internet service you sign up for is also a factor to consider when it comes to protecting your data.
- Shared Internet is the most common and is mainly used for services such as streaming music, movies, parental control and remote monitoring. However, a home network works through a shared connection that has a lower cost. However, this is not a recommended option for companies, because it presents unstable signals, with difficulty in maintaining download and upload traffic.
Other negative points are the decrease in speed as the number of users increases and the difficulty of reaching the full contracted speed.
- Dedicated Internet is a connection specially developed for the business sector. The difference between this connection and traditional broadband is the quality of navigation. The dedicated Internet, regardless of the size, guarantees a more secure, stable and high scale access. Through this type of connection, the company is connected to a router port, which eliminates network traffic and allows better system performance.
In summary, this is what your network architecture should looks like:
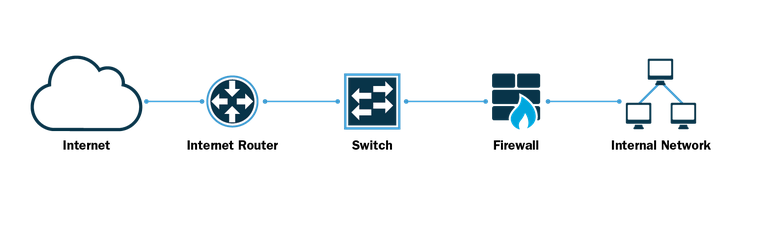
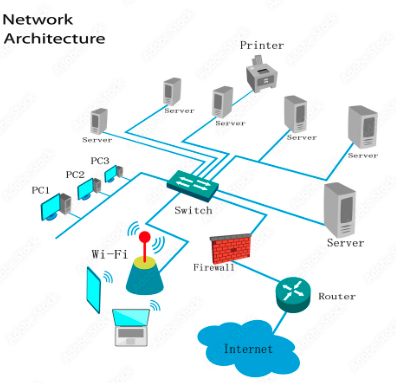
REMEMBER! Before making any decision about the security of your networks, it is highly recommended to talk to an IT network specialist for a personalized study and to guide you in the best way. In addition, the brands and characteristics of each component also influence the degree of security, there are brands that are more secure than others and thus their cost.
So, what is the safest way to connect my virtual assistant?
Virtual Assistance means that a person who is physically outside the host network – anywhere in the world – can have access to your information to perform specific professional tasks according to their role, connected via Internet.
Therefore, the most secure way for an «external» person to connect to your host network is through a VPN and ideally that person should also have the «standard» protocol in place. However, in reality, most virtual assistants have a shared Internet service and will hardly be able to install the standard components at home.
IT- Network Security for Law Firms
What is a VPN? A Virtual Private Network is a mechanism for creating a secure connection between a computing device and a computer network, or between two networks, using an insecure communication medium such as the public/shared Internet.
Without a VPN, the VA’s internet activity can be easily seen and intercepted by others. This includes their browsing history, downloaded files, internet banking details and passwords.
Or worse, hackers can trace the information back to their device through their internet protocol address (IP address). Their IP address reveals your physical location and can be used to track them in real life.

BUT when your VA connects to a VPN, their Internet activity will be encrypted and their real IP address will be masked. No one can see who they are or what they are doing, not even ISPs (Internet Service Providers), governments or hackers.

If in addition to all this, you want to be doubly protected, you can also take advantage of a Cyber-insurance, as an additional but never as the only option to protect your information.
Cyber-insurance is a specialty insurance product intended to protect businesses from Internet-based risks. Coverage provided by a cyber-insurance policies may include first-party coverage against losses such as data destruction, extortion, theft, hacking, and denial of service attacks; liability coverage indemnifying companies for losses to others caused, for example, by errors and omissions, failure to safeguard data, or defamation; and other benefits including regular security-audit, post-incident public relations and investigative expenses, and criminal reward funds.
REMEMBER! Before making any decision about the security of your networks, it is highly recommended to talk to an IT network specialist for a personalized study and to guide you in the best way. This article is only for reference purposes and does not constitute a specialized recommendation.
Outsourcing Virtual Assistants
If you are already at this stage and are looking for a professional Virtual Assistant to complement your team, learn about our customer service, paralegal assistants and marketing assistant plans.
See more valuable content to grow your law firm:
Hiring Employees in Mexico How does the Virtual Assistant hiring...
Read MoreLawyers who have optimized their websites with SEO to take...
Read MoreHow to grow in a highly competitive market? Here are...
Read MoreHow To Save Time and Money with Marketing Outsourcing for Law Firms Today
Marketing outsourcing for Law Firms How can I get help...
Read More



